Overview
External Identity enables you to:- Authenticate using existing identity provider (Okta, Azure AD)
- Control RBAC access to TrueFoundry resources (e.g., Models, MCP Servers, Agents, etc.)
- No need to create TrueFoundry user accounts
External Identity requires an identity provider to be configured.
When to Use External Identity
Organizations with existing identity providers (Okta, Azure AD) can use External Identity. Common scenarios:- B2B applications: Your customers authenticate through their own Identity Provider (IdP)
- No TrueFoundry accounts: Users who aren’t in TrueFoundry need Model, MCP, Agent access
How External Identity Works
- User/application authenticate and get a JWT token from the identity provider.
- User/application adds the JWT token as Bearer authorization header in TrueFoundry API’s
- TrueFoundry validates the token against the configured identity provider.
- TrueFoundry extracts claims from the token and maps it to external identity based on the claims configured.
- The selected external identity is used for RBAC when accessing TrueFoundry resources
- TrueFoundry uses the
subclaim to uniquely identify each user and manage their authentication for MCP Servers for personalization.
TrueFoundry never handles user credentials. Your identity provider remains the
source of truth for identity.
Prerequisites
Before creating an external identity, you must configure Identity Provider.Creating an Identity Provider
Fill the form
Configure the identity provider with config for JWT token validation. The form contains following fields: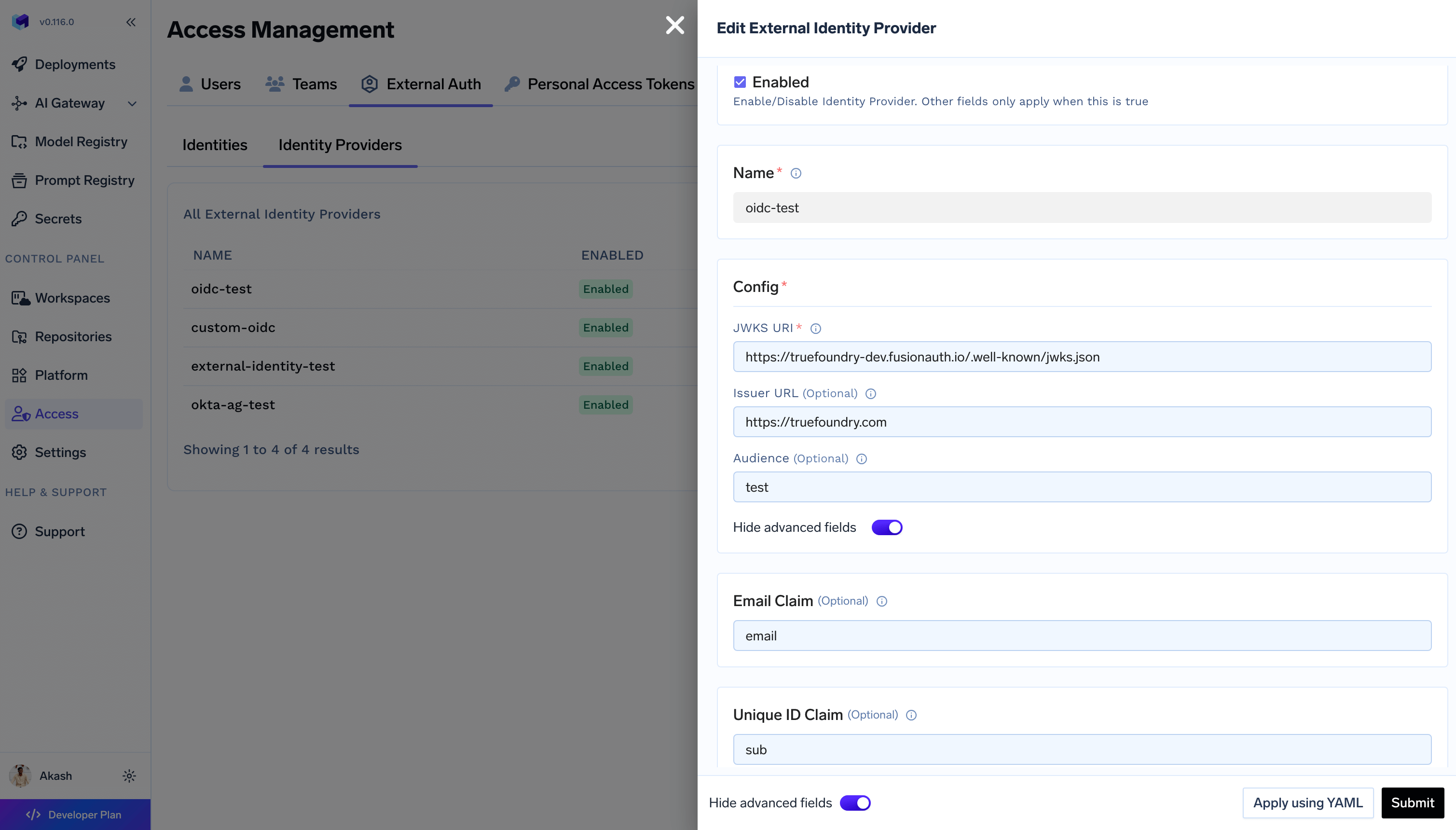
A unique name to identify this external identity provider. Should follow the
format as Alphanumeric characters and hyphens.
The name should be descriptive and help you identify the purpose of this
external identity.
Contains JWKS URI that exposed the JWKS for fetching the public key to validate the JWT token.
(Optional) You can also validate the token against the issuer and audience.
Advanced Options
You can configure claim keys for
unique id and email. Defaults are sub and email respectively.sub claim is mandatory for the token to be validated. You can change the
claim key under Advanced Settings.
Examples
Okta
Note<okta-organization> is the organization name of the Okta.
Azure AD
Note<tenant-id> and <client-id> are the tenant ID and client ID of the Azure AD application.
Creating an External Identity
Fill in the form
The form contains the following fields: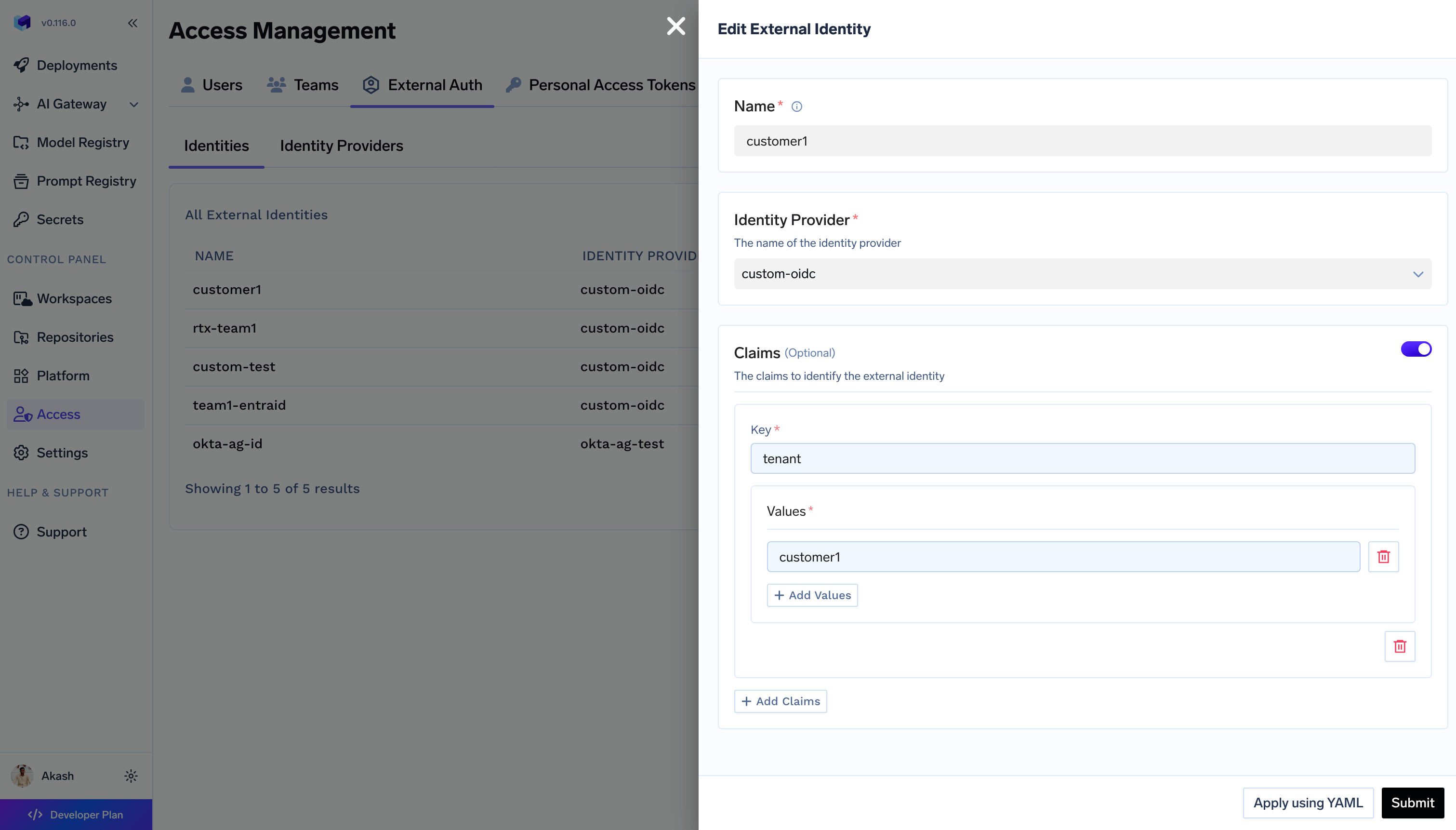
A unique name to identify this external identity. Should follow the format as alphanumeric characters and hyphens. Examples:
api-service, external-app, partner-integrationThe name should be descriptive and help you identify the purpose of this
external identity.
Select the identity provider from the list of configured identity providers.
You can create multiple external identities using the same identity provider.
When Truefoundry gets a token from the external identity, it will validate the
token against the identity provider and assign it to all the matching external
identity.

Using External Identity as Collaborator
Once created, external identities can be added as collaborators to TrueFoundry resources, granting them access based on the assigned role, similar to how you add users and teams as collaborators.Adding External Identity as Collaborator
Navigate to the Resource
Navigate to the resource you want to grant access to (e.g., Model, MCP Server,
Workspace, Cluster, etc.)
Add Collaborator
Click Add Collaborator in the collaborator selection and search for your
*External Identity. Choose the appropriate Role (e.g., Viewer, Editor,
Manager).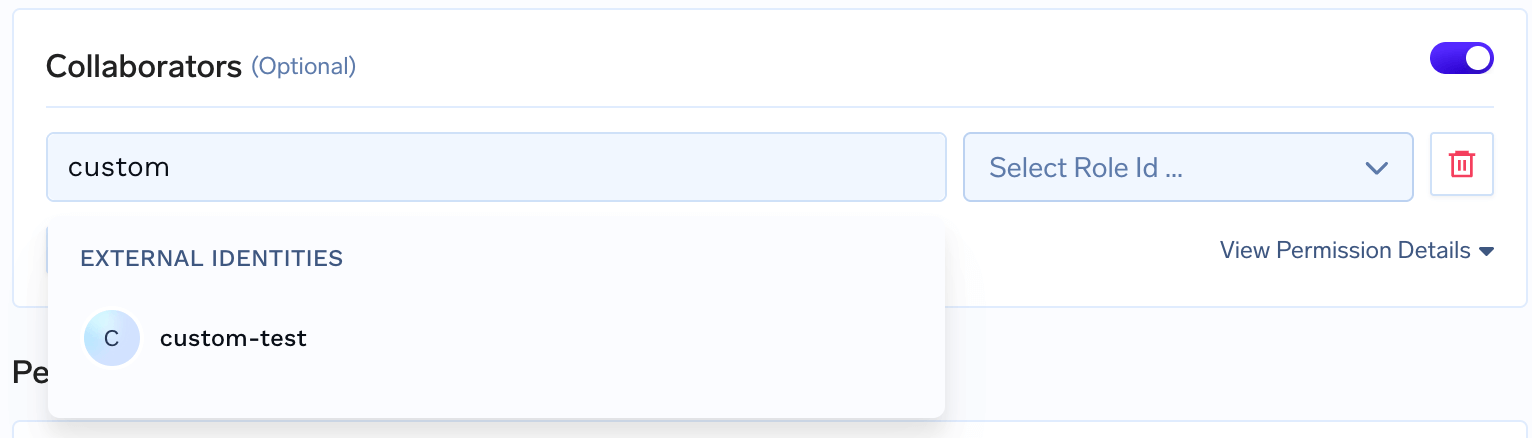

Troubleshooting
External Identity Not Matching
Problem: Token authentication fails or wrong external identity is selected. Solutions:- verify the JWKS URI is correct and the JWKS is accessible by TrueFoundry.
- verify the token issuer and audience in the token are correct if configured.
- verify the
subclaim is present in the token and is correct. - verify the identity provider is correct and matches your identity provider configuration name