Controlling Request Logging
Using HTTP Headers
To enable logging for a specific request, include theX-TFY-LOGGING-CONFIG header:
Using Environment Variables
Environment variable configuration is only available when running a self-hosted instance of TrueFoundry AI Gateway
REQUEST_LOGGING_MODE environment variable in the AI Gateway:
| Mode | Description |
|---|---|
HEADER_CONTROLLED | Logging depends on the enabled value in the X-TFY-LOGGING-CONFIG header. If the header is absent or set to true, logging will occur. If set to false, no logging will happen. |
ALWAYS | All requests are logged regardless of the enabled value. |
NEVER | No requests are logged regardless of the enabled value. |
Viewing Request Logs
You can view all logged requests in the TrueFoundry UI. Go toAI Gateway > Monitor > Requests
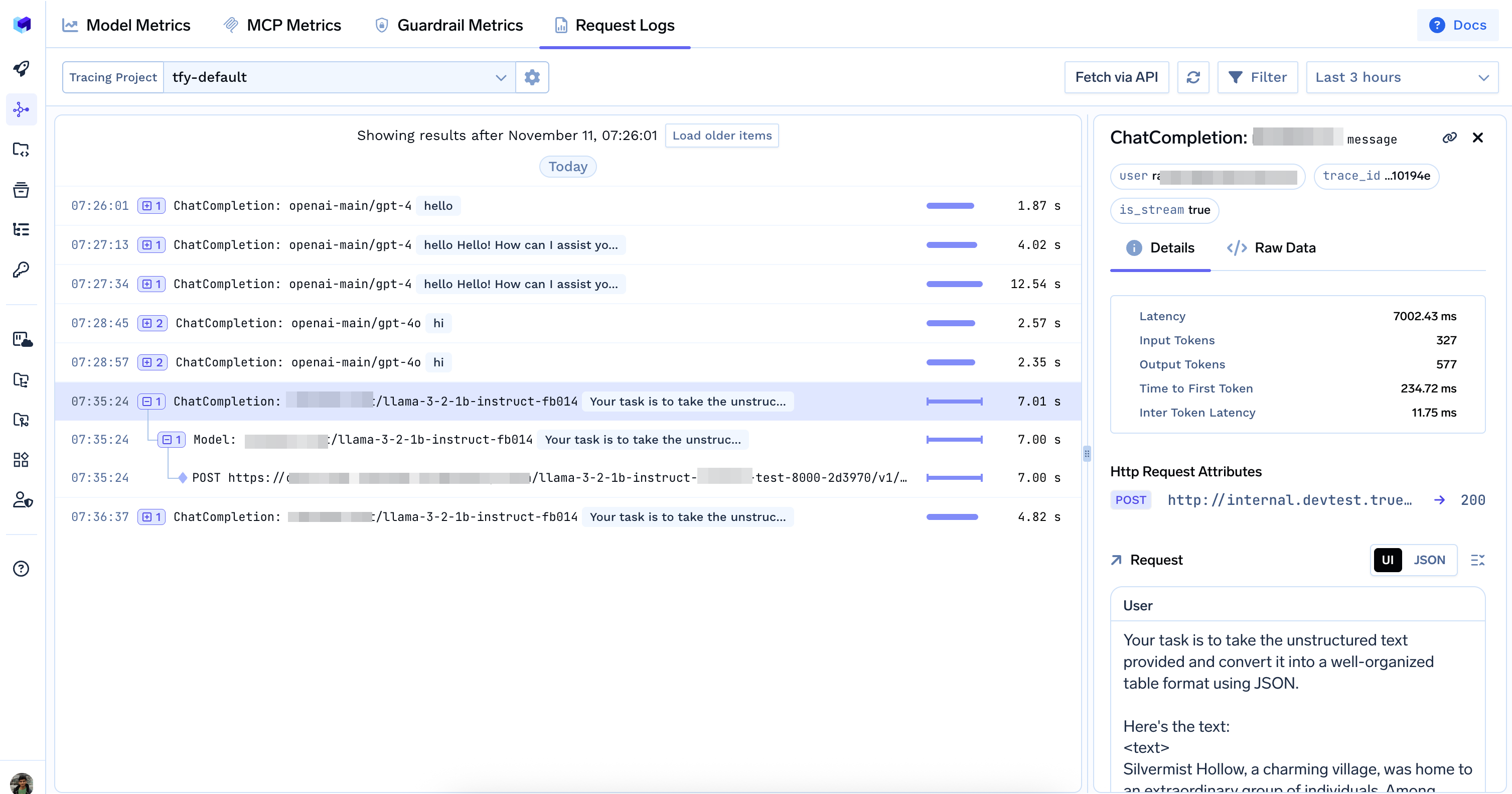
Code Example
Data Access Rules for Request Logs and Metrics
Data Access Rules allow you to control who can access which request logs and metrics in the AI Gateway. Gateway Datasets provide access to subsets of traces and metrics by applying filters, enabling fine-grained access control based on users, teams, roles, and data scopes.Overview
Data Access Rules define:- Who can access data (subjects: users, teams, or roles)
- What type of data the rule applies to (Traces, Metrics, or both)
- What data they can access (scope: own data, team data, or all data)
- Optional filters to further restrict access (for all data scope)
How It Works
- Each user’s access to request logs and metrics is evaluated against all enabled rules
- Users can access data if they match any rule’s subjects and scope
- Rules are evaluated independently—matching multiple rules grants access to the union of their scopes
- Disabled rules are ignored during access evaluation
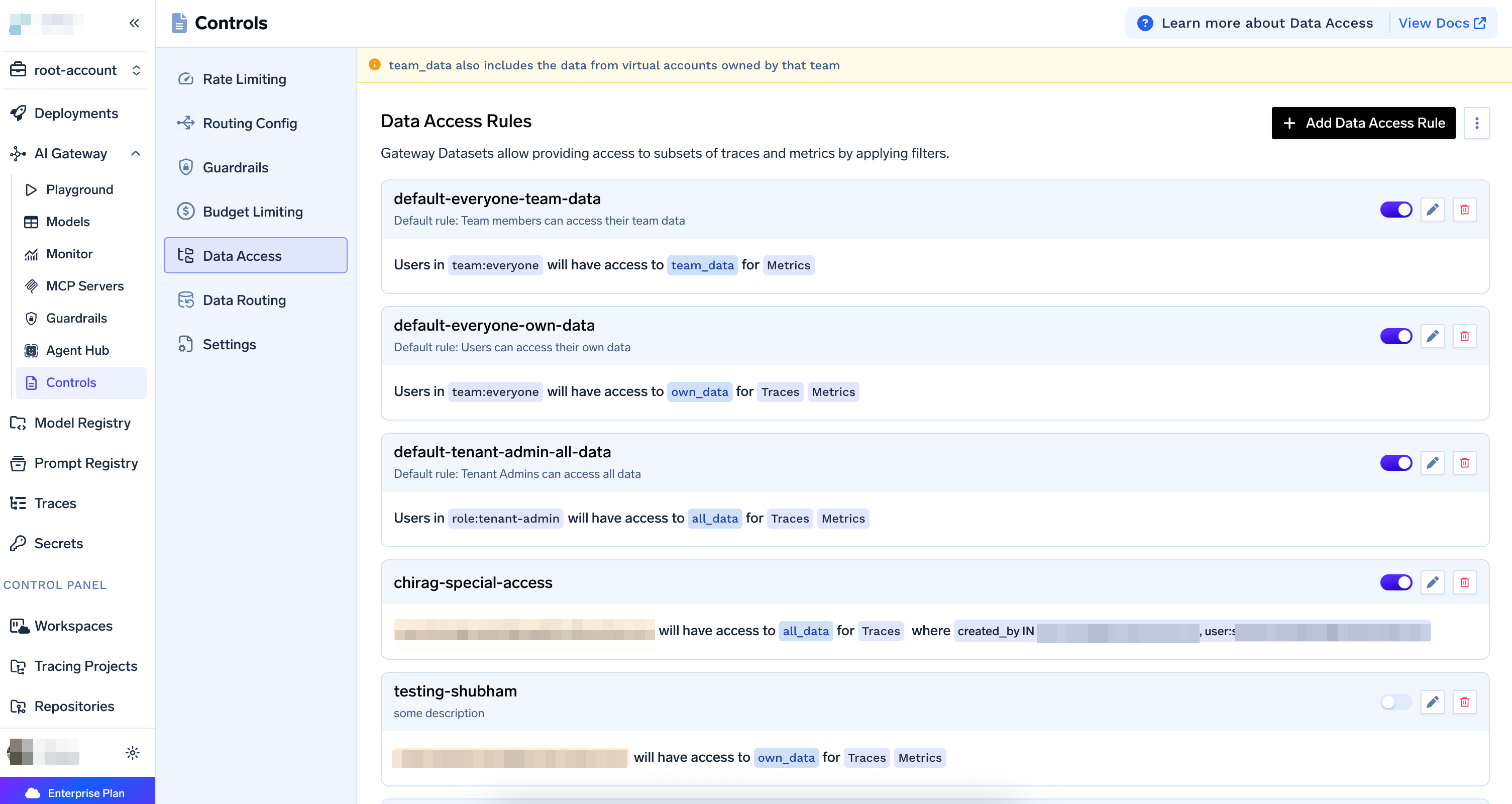
Accessing Data Access Rules
Navigate toAI Gateway > Controls > Data Access to view and manage your data access rules.
Configuration Methods
Data Access Rules can be configured in two ways:- Via UI: Use the Data Access interface to create, edit, and manage rules visually
- Via YAML Config: Define rules in a YAML configuration file (similar to rate limiting and budget limiting)
Default Rules
TrueFoundry AI Gateway comes with three default rules:-
default-everyone-team-data: Team members can access their team data- Subjects:
team:everyone - Scope:
team_data - Data Types: Metrics
- Subjects:
-
default-everyone-own-data: Users can access their own data- Subjects:
team:everyone - Scope:
own_data - Data Types: Traces, Metrics
- Subjects:
-
default-tenant-admin-all-data: Tenant Admins can access all data- Subjects:
role:tenant-admin - Scope:
all_data - Data Types: Traces, Metrics
- Subjects:
Data Types
Data Access Rules let you specify which types of data each rule applies to:- Traces: Request logs and trace data from AI Gateway requests
- Metrics: Aggregated metrics and monitoring data
Data Scopes
Data Access Rules support three scopes that define what data users can access:Own Data (own_data)
Users can only access request logs and metrics they created themselves.
Use cases:
- Individual developers viewing their own requests
- Personal debugging and monitoring
Team Data (team_data)
Users can access request logs and metrics from all members of their team, including data from virtual accounts owned by that team.
Use cases:
- Team leads monitoring team-wide usage
- Collaborative debugging across team members
- Team-level analytics and reporting
team_data includes data from virtual accounts owned by the team, making it easy to track all team-related activity.All Data (all_data)
Users can access all request logs and metrics across the entire organization, with optional filters to restrict access.
Use cases:
- Administrators managing organization-wide data
- Cross-team analytics and reporting
- Compliance and auditing requirements
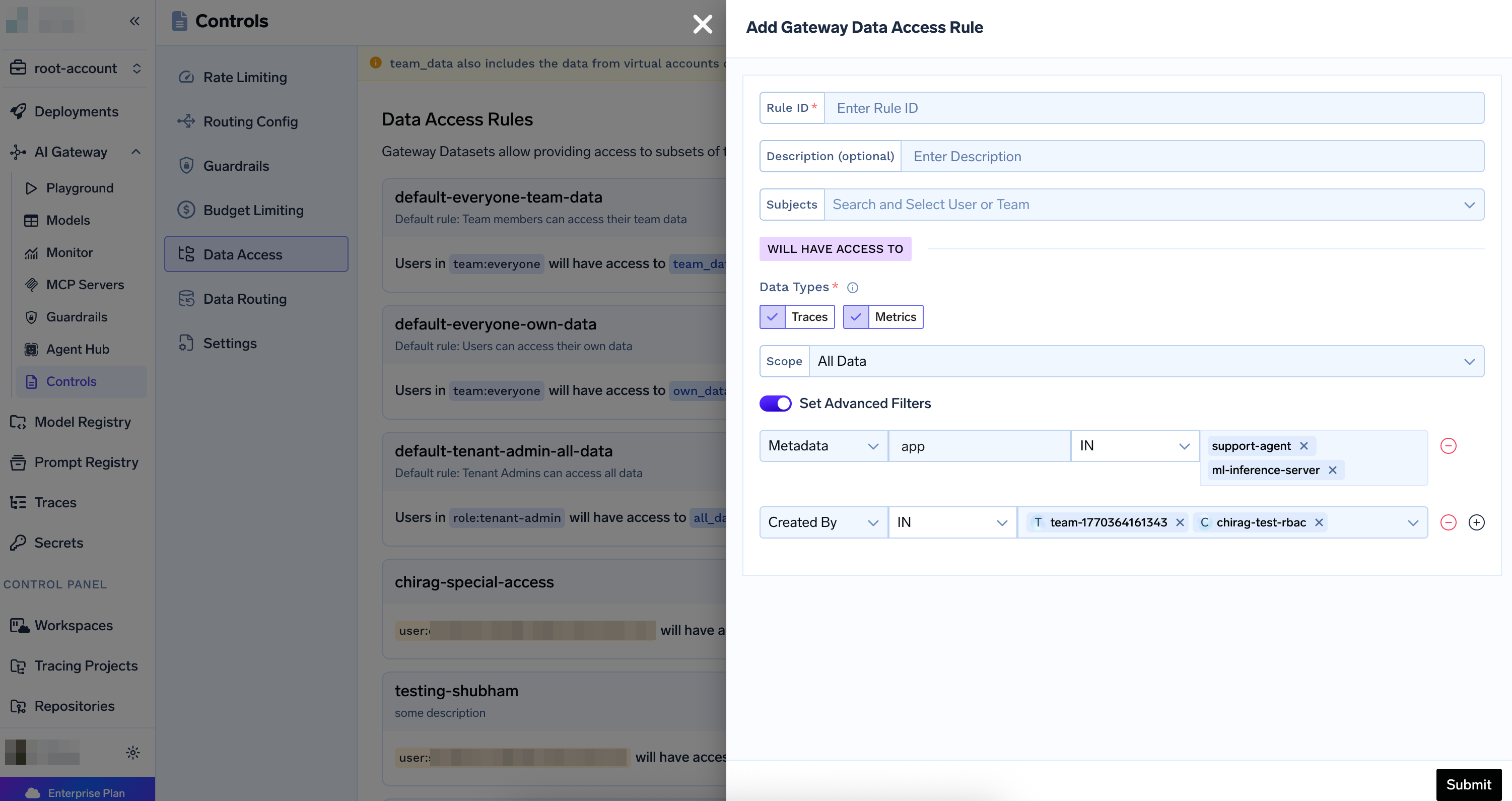
all_data scope, you can optionally add filters to restrict access:
- Metadata Filters: Filter by custom metadata keys from the
X-TFY-METADATAheader- Example:
application_name IN (support-agent, ml-inference-server)
- Example:
- Created By Filters: Filter by who created the data
- Example:
created_by IN (team-1766965687056, user:john-doe)
- Example:
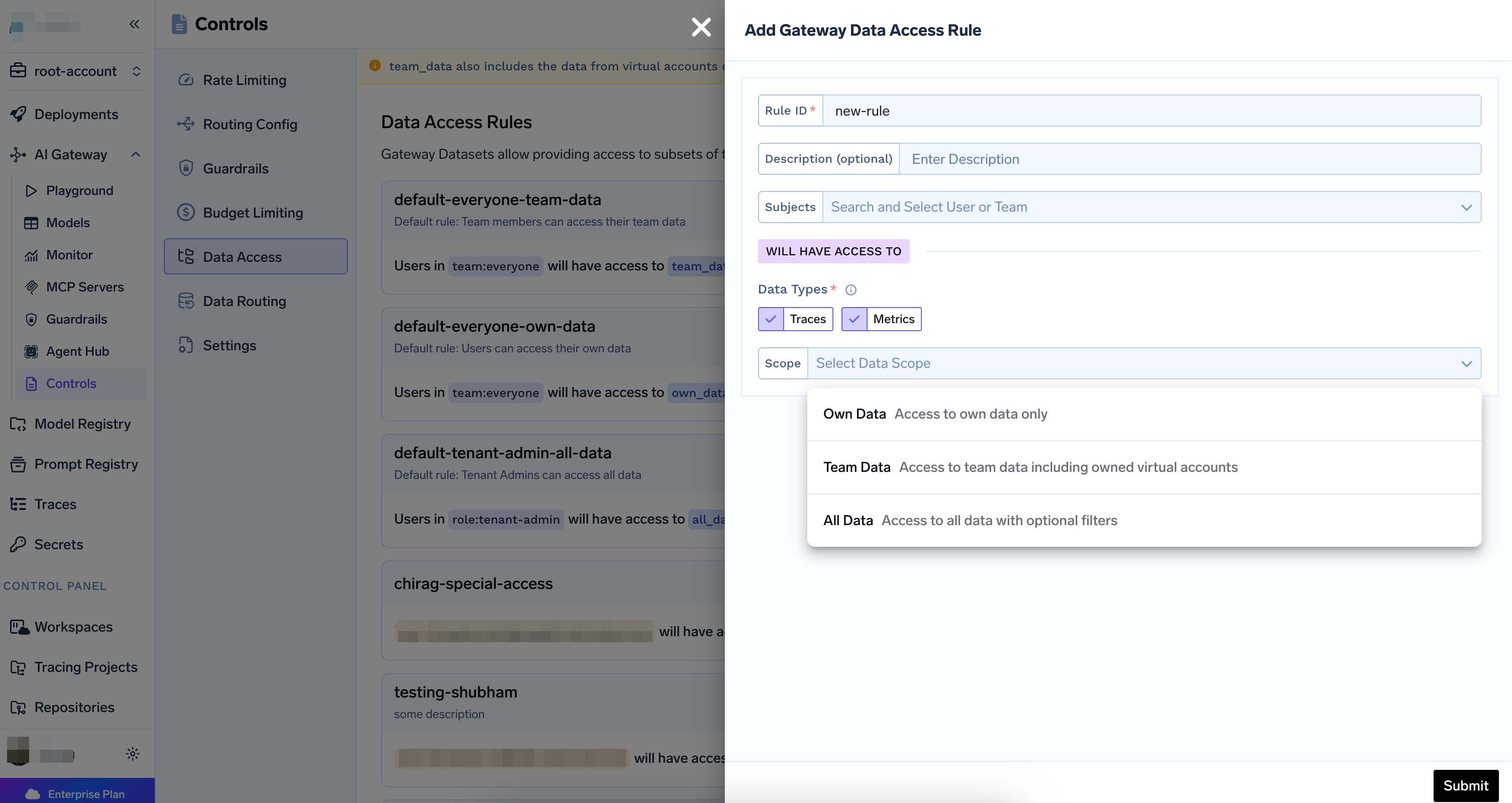
Creating a Data Access Rule
Select Subjects
Choose who this rule applies to: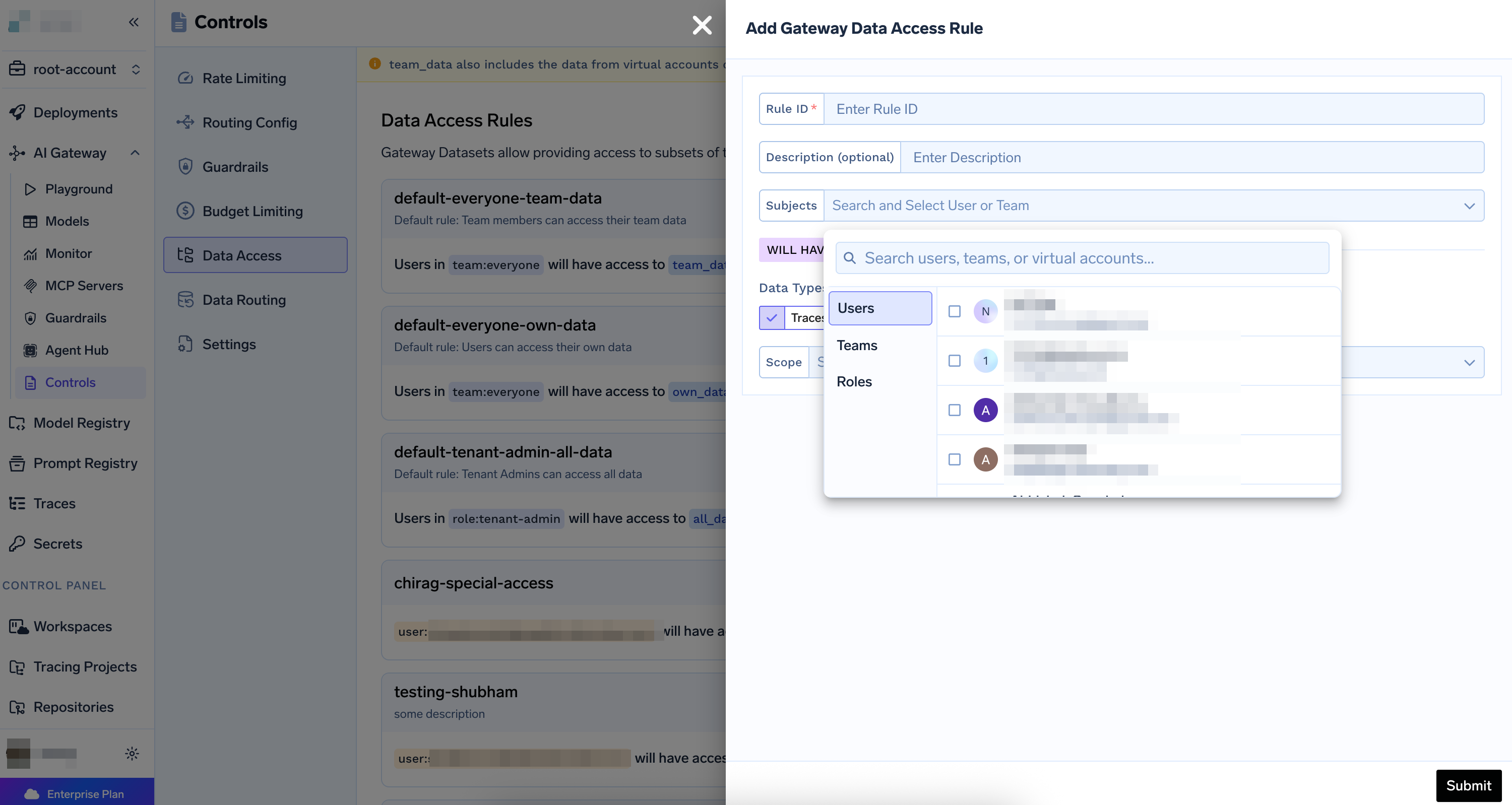
- Users: Specific users (e.g.,
user:alice@example.com) - Teams: Team members (e.g.,
team:engineering) - Roles: Users with specific roles (e.g.,
role:tenant-admin)

Select Data Types
Choose which types of data this rule applies to:
- Traces: Request logs and trace data
- Metrics: Aggregated metrics and monitoring data
Choose Scope
Select the data scope:
- Own Data: Access to own data only
- Team Data: Access to team data including owned virtual accounts
- All Data: Access to all data with optional filters
Configure Advanced Filters (Optional)
If you selected All Data, you can optionally enable advanced filters:
- Toggle “Set Advanced Filters” to ON
- Add metadata filters (e.g., filter by
application_name) - Add created by filters (e.g., filter by specific users or teams)
- Add multiple filter conditions as needed

Rule Components
Rule ID (id)
A unique identifier for the rule. Used for reference in logs and the UI.
Requirements:
- Must be unique across all rules
- Can contain letters, numbers, hyphens
- Must start with a letter
Description (description)
Optional human-readable description explaining the rule’s purpose.
Data Types (data_types)
Specifies which types of data the rule applies to. At least one must be selected.
Available types:
| Type | Description |
|---|---|
traces | Request logs and trace data from AI Gateway |
metrics | Aggregated metrics and monitoring data |
Subjects (subjects)
List of users, teams, or roles that this rule applies to.
Format:
- Users:
user:usernameoruser:email@example.com - Teams:
team:team-name - Roles:
role:role-name(e.g.,role:tenant-admin)
Scope (scope)
Defines what data the subjects can access.
Available scopes:
| Scope | Description |
|---|---|
own_data | Access to own data only |
team_data | Access to team data including owned virtual accounts |
all_data | Access to all data with optional filters |
Filters (filters) - Optional
Only applicable for all_data scope. Further restricts which data can be accessed.
Filter Types:
-
Metadata Filter: Filter by custom metadata keys
-
Created By Filter: Filter by who created the data
IN: Matches if the value is in the provided list
Enabled (enabled)
Whether the rule is active. Disabled rules are ignored during access evaluation.
Default: true
Managing Rules
Enable/Disable Rules
Toggle the switch on any rule card to enable or disable it. Disabled rules are not evaluated when checking data access.Edit Rules
Click the edit icon (pencil) on a rule card to modify its configuration.Delete Rules
Click the delete icon (trash can) on a rule card to remove it. Default rules can also be deleted if needed.Examples
Basic Rules
Basic Rules
Simple rules for common access patterns.
Filtered All Data Access
Filtered All Data Access
Rules with advanced filters to restrict all data access.
When using metadata filters, ensure requests include the
X-TFY-METADATA header with the relevant keys. For example:Multi-Subject Rules
Multi-Subject Rules
Rules that apply to multiple users, teams, or roles.
Virtual Account Access
Virtual Account Access
Rules that include virtual account data through team_data scope.
When using
team_data scope, virtual accounts owned by the team are automatically included. No additional configuration needed.Best Practices
- Start with default rules: The default rules cover most common use cases. Only create custom rules when you need specific access patterns.
-
Use the most restrictive scope: Prefer
own_dataorteam_dataoverall_datawhen possible. Only useall_datawhen necessary. -
Restrict data types when appropriate: Use
data_typesto limit rules to only Traces or only Metrics when full access to both isn’t needed (e.g., metrics-only access for dashboard viewers). -
Leverage filters: When using
all_data, always add filters to restrict access to only what’s needed. - Document your rules: Use descriptive rule IDs and descriptions to make it clear what each rule does.
- Test before disabling: Before disabling or deleting a rule, verify that users have alternative access paths.
- Review regularly: Periodically review your data access rules to ensure they align with your organization’s access control policies.
-
Use roles for admin access: Prefer
role:tenant-adminover individual users for administrative access to all data.
Troubleshooting
Users can’t see expected data:- Verify the rule is enabled
- Check that the user matches one of the rule’s subjects
- Ensure the rule’s
data_typesincludes the data type they’re trying to access (Traces or Metrics) - Ensure the data scope includes the data they’re trying to access
- For
all_datawith filters, verify the data matches the filter conditions
- Review rules and ensure you’re using the most restrictive scope
- Add filters to
all_datarules to narrow access - Consider using
team_datainstead ofall_datawhen possible
- Ensure you’re using
team_datascope (which includes virtual accounts) - Or use
all_datawith acreated_byfilter for the virtual account